
If you're looking for an IT security resume example, you've come to the right place. We've put together a good Cyber and IT security resume sample as well as some important tips to ensure you capture the attention of a hiring manager.
According to Payscale:
Information security analysts are responsible for providing security solutions for their companies. Their main duties include doing research, collecting data, developing secure strategies and maximizing productivity. They also are in charge of implementing security principles while following strict privacy policies. Information security analysts have advanced skills when it comes to finding security threats and other vulnerabilities. They conduct assessments of enterprise environments and frequently monitor logs and computer traffic.
For an updated resume format to use in 2020, head over to this post instead: Cybersecurity Resume Example from Zipjob.
IT Security Resume Sample:
(Text Version Below)
Expert Tip
View 200+ more professional resume samples for all industries, along with a guide to writing resumes from our career experts.
Tips For Writing an IT Security Resume
1. Write a resume summary
Don't use an objective as those are outdated and boring, you should instead lead with a strong summary. A resume summary should tell the employer a bit about who you are, how you're qualified and why you'd make a good fit for the position. Be sure to mention some achievements from your previous positions.
2. Utilize a core competencies section
A core competencies section on a resume is effective for both getting past an ATS and capturing the attention of a hiring manager. An ATS is a resume parsing software utilized by most employers and a core competencies section allows you to keyword optimize your resume with industry/position related keywords it may be searching for. Tailoring your resume and swapping your keywords in and out is also a breeze when you utilize core competencies.
3. Focus on your achievements
Always try to focus on past achievements rather than simply listing out duties and responsibilities from previous positions. Simply choosing the right wording can even make your duties look like accomplishments. Utilize powerful action verbs to ensure your resume is achievement focused.
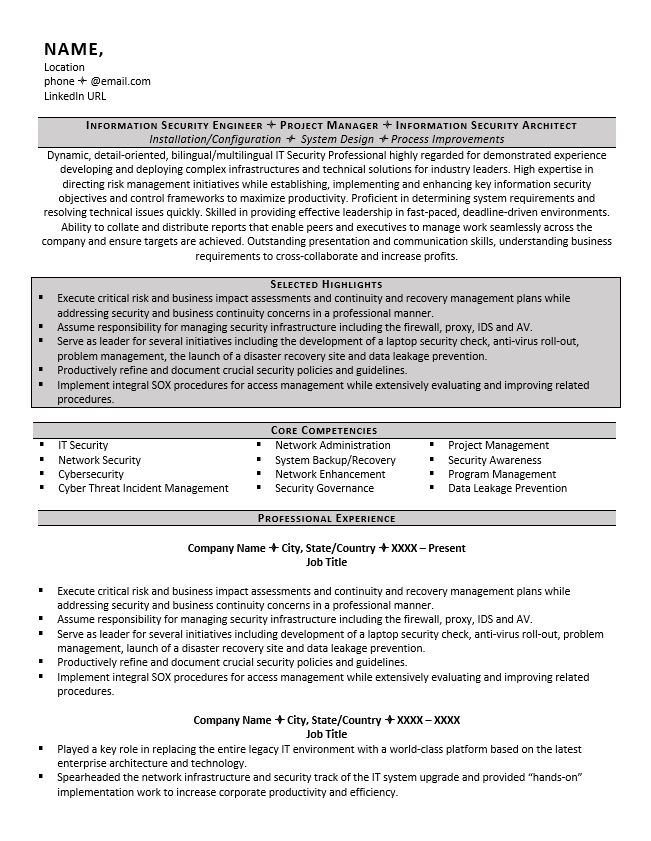
IT Security Resume Example - Text Version:
Information Security Engineer Project Manager Information Security Architect
Installation/Configuration System Design Process Improvements
Summary:
Dynamic, detail-oriented, bilingual/multilingual IT Security Professional highly regarded for demonstrated experience developing and deploying complex infrastructures and technical solutions for industry leaders. High expertise in directing risk management initiatives while establishing, implementing and enhancing key information security objectives and control frameworks to maximize productivity. Proficient in determining system requirements and resolving technical issues quickly. Skilled in providing effective leadership in fast-paced, deadline-driven environments. Ability to collate and distribute reports that enable peers and executives to manage work seamlessly across the company and ensure targets are achieved. Outstanding presentation and communication skills, understanding business requirements to cross-collaborate and increase profits.
Selected Highlights
Execute critical risk and business impact assessments and continuity and recovery management plans while addressing security and business continuity concerns in a professional manner.
Assume responsibility for managing security infrastructure including the firewall, proxy, IDS and AV.
Serve as leader for several initiatives including the development of a laptop security check, anti-virus roll-out, problem management, the launch of a disaster recovery site and data leakage prevention.
Productively refine and document crucial security policies and guidelines.
Implement integral SOX procedures for access management while extensively evaluating and improving related procedures.
Core Competencies/ Skills
IT Security
Network Administration
Project Management
Network Security
System Backup/Recovery
Security Awareness
Cyber security
Network Enhancement
Program Management
Cyber Threat Incident Management
Security Governance
Data Leakage Prevention
Professional Experience
Company Name City, State/Country XXXX – Present
Job Title
Execute critical risk and business impact assessments and continuity and recovery management plans while addressing security and business continuity concerns in a professional manner.
Assume responsibility for managing security infrastructure including the firewall, proxy, IDS and AV.
Serve as leader for several initiatives including development of a laptop security check, anti-virus roll-out, problem management, launch of a disaster recovery site and data leakage prevention.
Productively refine and document crucial security policies and guidelines.
Implement integral SOX procedures for access management while extensively evaluating and improving related procedures.
Company Name City, State/Country XXXX – XXXX
Job Title
Played a key role in replacing the entire legacy IT environment with a world-class platform based on the latest enterprise architecture and technology.
Spearheaded the network infrastructure and security track of the IT system upgrade and provided “hands-on” implementation work to increase corporate productivity and efficiency.
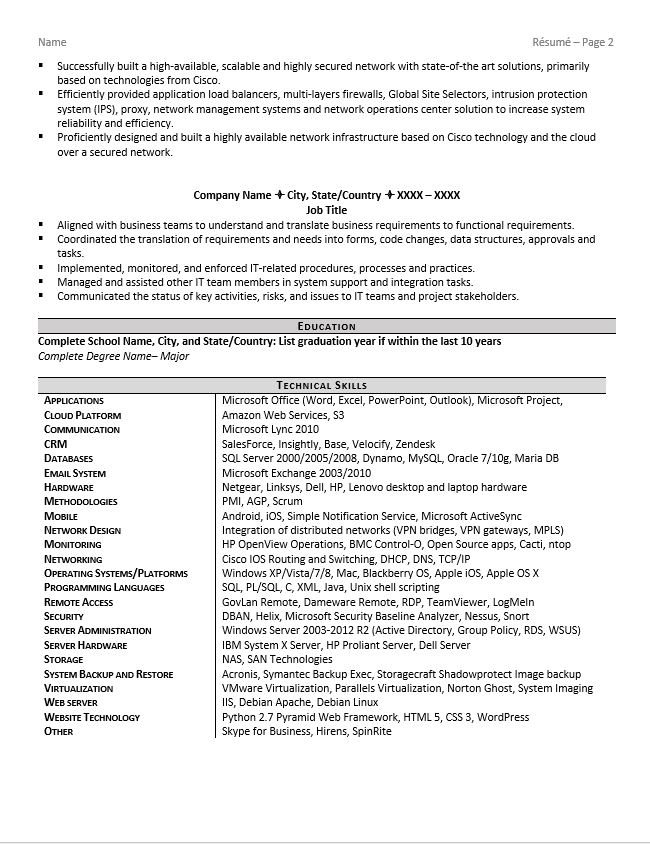
Successfully built a high-available, scalable and highly secured network with state-of-the art solutions, primarily based on technologies from Cisco.
Efficiently provided application load balancers, multi-layers firewalls, Global Site Selectors, intrusion protection system (IPS), proxy, network management systems and network operations center solution to increase system reliability and efficiency.
Proficiently designed and built a highly available network infrastructure based on Cisco technology and the cloud over a secured network.
Company Name City, State/Country XXXX – XXXX
Job Title
Aligned with business teams to understand and translate business requirements to functional requirements.
Coordinated the translation of requirements and needs into forms, code changes, data structures, approvals and tasks.
Implemented, monitored, and enforced IT-related procedures, processes and practices.
Managed and assisted other IT team members in system support and integration tasks.
Communicated the status of key activities, risks, and issues to IT teams and project stakeholders.
Education
Complete School Name, City, and State/CountryComplete Degree Name– Major
Technical Skills
Applications
Microsoft Office (Word, Excel, PowerPoint, Outlook), Microsoft Project,
Cloud Platform
Amazon Web Services, S3
Communication
Microsoft Lync 2010
CRM
SalesForce, Insightly, Base, Velocify, Zendesk
Databases
SQL Server 2000/2005/2008, Dynamo, MySQL, Oracle 7/10g, Maria DB
Email System
Microsoft Exchange 2003/2010
Hardware
Netgear, Linksys, Dell, HP, Lenovo desktop and laptop hardware
Methodologies
PMI, AGP, Scrum
Mobile
Android, iOS, Simple Notification Service, Microsoft ActiveSync
Network Design
Integration of distributed networks (VPN bridges, VPN gateways, MPLS)
Monitoring
HP OpenView Operations, BMC Control-O, Open Source apps, Cacti, ntop
Networking
Cisco IOS Routing and Switching, DHCP, DNS, TCP/IP
Operating Systems/Platforms
Windows XP/Vista/7/8, Mac, Blackberry OS, Apple iOS, Apple OS X
Programming Languages
SQL, PL/SQL, C, XML, Java, Unix shell scripting
Remote Access
GovLan Remote, Dameware Remote, RDP, TeamViewer, LogMeIn
Security
DBAN, Helix, Microsoft Security Baseline Analyzer, Nessus, Snort
Server Administration
Windows Server 2003-2012 R2 (Active Directory, Group Policy, RDS, WSUS)
Server Hardware
IBM System X Server, HP Proliant Server, Dell Server
Storage
NAS, SAN Technologies
System Backup and Restore
Acronis, Symantec Backup Exec, Storagecraft Shadowprotect Image backup
Virtualization
VMware Virtualization, Parallels Virtualization, Norton Ghost, System Imaging
Web server
IIS, Debian Apache, Debian Linux
Website Technology
Python 2.7 Pyramid Web Framework, HTML 5, CSS 3, WordPress
Other
Skype for Business, Hirens, SpinRite

Written by
ZipJob Team
The ZipJob team is made up of professional writers located across the USA and Canada with backgrounds in HR, recruiting, career coaching, job placement, and professional writing.
